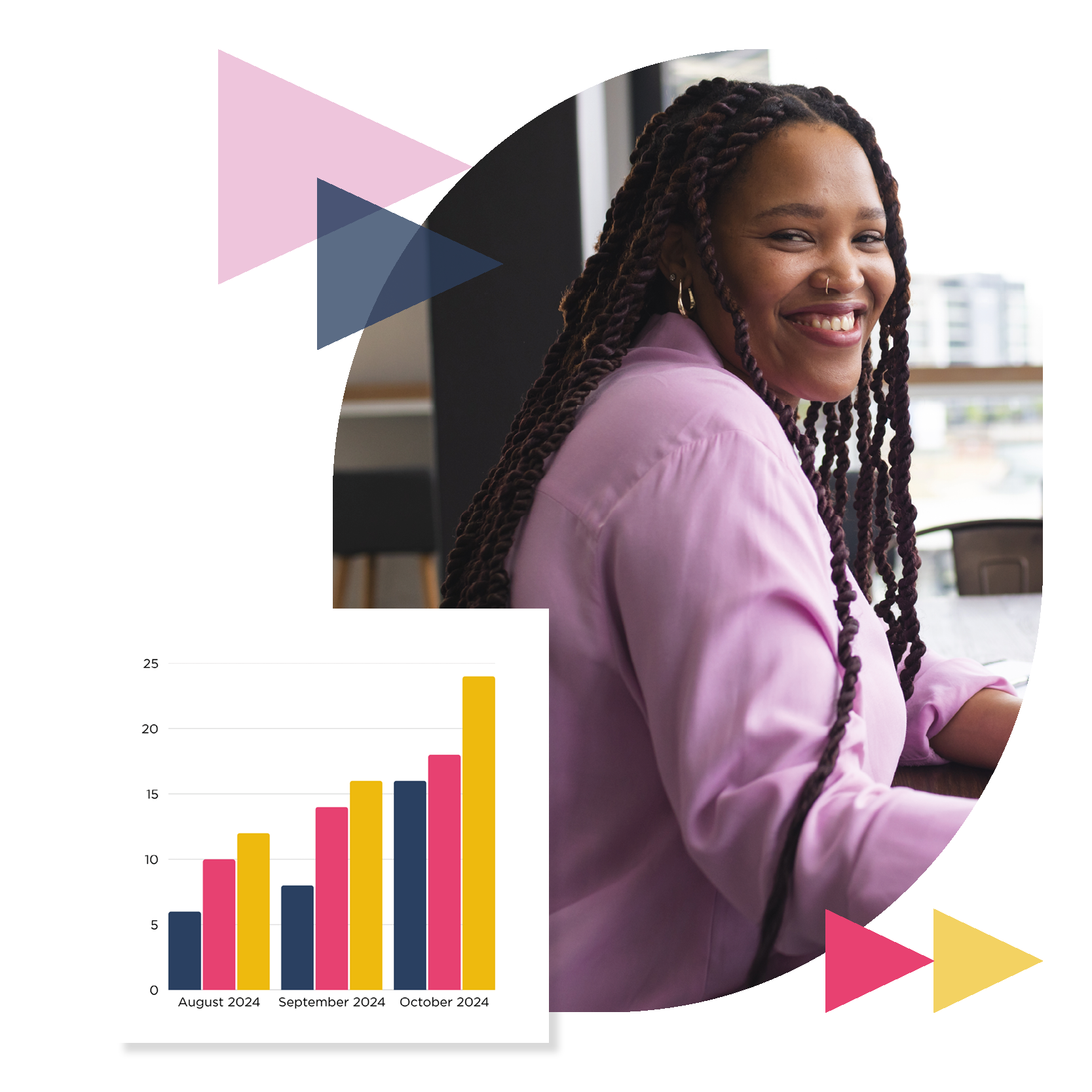
Security vulnerabilities
Explore best practices for patching, shadow IT detection, and lifecycle management to protect your organization.
Organizations are constantly being exploited by cyber criminals. Recognizing this risk and taking action to protect yourself is the key to keeping your organization, employees, and customers safe.
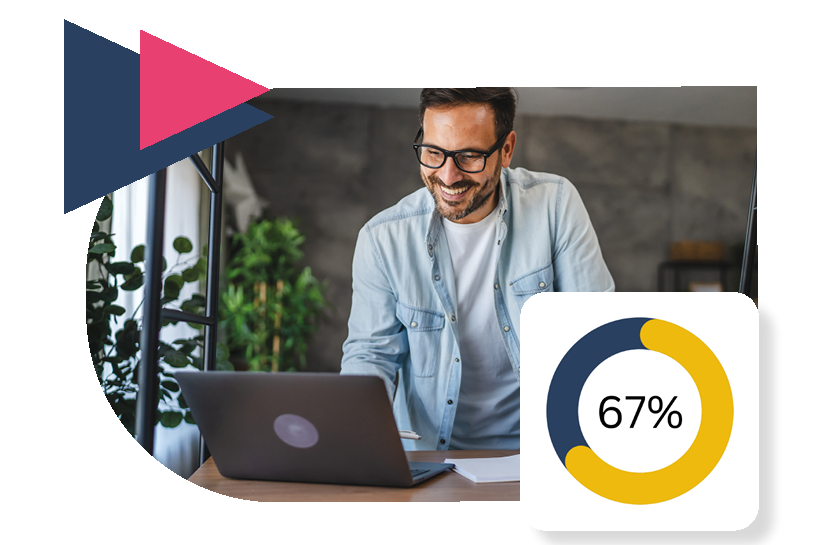
Several factors could be putting your organization at risk:
- Unpatched software: outdated applications lacking the latest security updates create easy entry points for attackers
- Shadow IT: unauthorized software installations bypass protocols, increasing vulnerabilities
- License mismanagement: unsupported or expired licenses often lack critical security updates
- Inventory management: inaccurate software inventories make it difficult to identify vulnerabilities

How SAM solutions help solve security vulnerabilities
On top of this, detecting and managing shadow IT prevents unauthorized software from becoming a vulnerability.
- Enhanced visibility
- Proactive patch management
- Shadow IT prevention
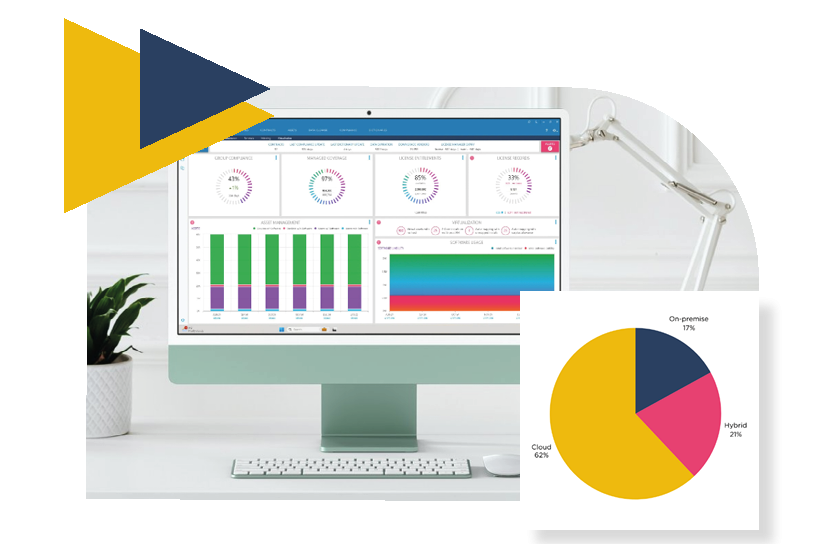
Security vulnerabilities FAQs
Common vulnerabilities include unpatched software, shadow IT, license mismanagement, and inaccurate inventory management.
Get in touch today to find out more and book a free demoSAM solutions enhance visibility into your software inventory, helping identify and address vulnerabilities to prevent them becoming a threat in future.
Get in touch today to find out more and book a free demoWant to find out more about security vulnerabilities? Talk to our specialists now.
Our specialists are here to help you explore best practices for patching, shadow IT detection, and lifecycle management to protect your organization. Get in touch to find out more.